JS Business Solutions Blog
One of the greatest challenges for businesses is how they protect themselves from threats, including both the physical and digital spaces. Worse yet, the responsibility falls on more than just your IT department. Every employee needs to know and understand how their actions impact operational continuity and business success.
Today’s businesses need an established cybersecurity strategy. It’s as simple as that.
However, many businesses need guidance to create this strategy, which is why the National Institute of Standards and Technology has developed a framework for proper cybersecurity protection. Let’s walk through this framework and discuss what you need to do to meet its requirements.
Business is built on relationships, and to be frank, some can be quite challenging. Think about all the difficulties you’ve faced with customers, vendors, or employees. Sometimes, it's hard to imagine how your business could succeed without these key players, but they all can be a drain on any given day. Today, we’ll explore how the relationships you build in business can be the deciding factor in your success.
Network bottlenecks can be a real problem for businesses that depend on significant data transmission as a part of their day-to-day operations. More companies than ever use a lot of different technologies that chew through bandwidth and it can cause their network to move slowly. Let’s go through some of the steps you should take to eliminate these network bottlenecks.
Small businesses often face a range of technology-related challenges that can disrupt the efficiency of their business. Being able to understand the common issues—such as network connectivity problems, outdated technology, or cybersecurity—is the first step toward keeping business running smoothly. By identifying these recurring problems, businesses can anticipate potential disruptions and prepare strategies to reduce their risk.
By now, you know that every business needs to prioritize its entire security footprint, including technology. The security technology used in businesses today has a huge effect on the overall security of an organization. This means that you have to have a coordinated effort that allows your security initiatives to consider your business’ IT. In today’s blog, we’ll show you how effective organizations consolidate their security using IT.
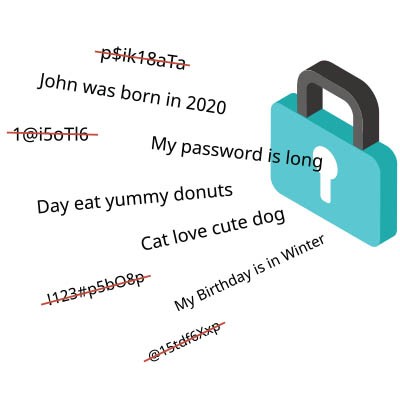
Strong passwords are extremely important these days. Cybercriminals only need low-end hardware to crack millions of passwords at once, so it's critical to use random, complex strings of characters.
The bigger problem most users have is using unique passwords for each and every account. Any account is liable to be compromised at any given time, and you might not even know about it. If your password is compromised, the bad guys can use it to access all of your other accounts.
Today’s businesses have to deal with many risk factors, especially cybersecurity and its many related concerns. At this year’s Cybsafe Impact 2024 USA conference, intended to share human risk management insights, a very accomplished panel of experts shared various thoughts.
Let’s explore some of the topics this panel spoke on.
Even if it didn’t directly affect you, you have probably heard about the Crowdsrike outage that caused critical errors in a lot of Microsoft-run systems. Due to the sheer volume of companies and organizations that are using Windows, this error caused an unprecedented amount of computers to crash and took down over 8.5 million systems for extended periods and cost some of the most successful businesses billions of dollars. It was also noteworthy for affecting air travel, causing 3,000 flights to be canceled and wreaking havoc on people’s travel plans. As the largest outage in world history, it made a lot of people realize that the technology that we all depend on for our livelihoods isn’t infallible. Today, let's take a look at some of the things we should take away from the CrowdStrike outage.
Without technology, your business cannot run the way it needs to. If a disaster strikes, there is no telling how much it could affect operations. For example, a hurricane or a cyberattack could disrupt operations to the point where your business cannot function the way it needs to. Today, we want to highlight some of the ways that a disaster recovery system can help you overcome these hurdles.
Prioritizing cybersecurity is mandatory for all business owners, but many don’t know where to start. As a result, many businesses deal with cybersecurity issues that can put them behind and even ruin a good thing. In today’s blog, we provide a guide that explains the basics of cybersecurity for anyone to follow.
For any organization that depends on its wireless network, your router is a critical piece of hardware that does more than you may realize. From broadcasting wireless Internet signals to protecting your network from harm, knowing exactly what to do with your router is good knowledge to have. Today, we’ll go through some of the things you should know about your router that will allow you to improve your organization's Wi-Fi significantly.
There are plenty of reasons why you might have employees working while out and about on travel, whether it’s for conferences, professional development sessions, or otherwise. Traveling with technology can be stressful and dangerous, though, particularly if you aren’t taking preventative measures. Today, we want to discuss what you can do to keep your entire team’s technology safe while they are traveling.
Getting your organization’s file-sharing policies and procedures right can make the difference between efficient, collaborative operations and inefficient and cost-wasting ones. This can get tricky, however. In today’s blog, we’ll go through some of the best practices your organization can implement to get the most out of its file sharing.
With the threat landscape littered with companies that don’t take their IT security seriously, it's hardly surprising that many are embracing what's known as a zero-trust policy to fortify their security measures. What exactly does zero-trust entail, and why does it prove so formidable in thwarting potential risks for your enterprise? Let's delve into this topic in today's blog post.